Abstract
The advent of network functions virtualization (NFV) has revolutionized numerous network-based applications due to its several benefits such as flexibility, manageability, scalability, and security. By the software-based virtualization of network functions on a single infrastructure, NFV provides users with a framework that dynamically provisions various network services in a flexible manner. However, NFV faces several security challenges (e.g., multi-tenancy and live migration) which make it vulnerable to some cybersecurity attacks (e.g., side-channel attacks and shared resource misuse attacks). In this paper, we provide an overview of NFV, discuss potentially serious security threats on NFV and introduce effective countermeasures to mitigate those threats. Finally, we suggest some practical solutions to provide a trustworthy platform for NFV.
1. Introduction
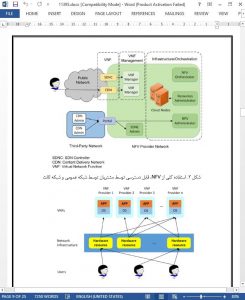
Nowadays, the impressive effects of network functions virtualization (NFV) are evident in the wide range of applications from IP node implementations (e.g., future Internet architecture) to mobile core networks [1]. NFV allows network functions (e.g., packet forwarding and dropping) to be performed in virtual machines (VMs) in a cloud infrastructure rather than in dedicated devices [2]. NFV as an agile and automated network is desirable for network operators due to the ability of easily developing new services and the capabilities of self-management and network programmability via software-defined networking (SDN) [3]. Furthermore, co-existence with current networks and services leads to improve customer experience, and reduces the complexity, capital expenditure (CAPEX), and operational expenditure (OPEX).
5. Conclusion
The considerable properties of NFV lead to a global trend that network functions are implemented in cloud through virtualization. NFV provides many benefits of the virtualization by introducing software-based appliances and utilizing cloud computing. Even with such many advantages and revenues, NFV also faces several significant security challenges driven by the virtualization and network infrastructure.
In order to understand those security challenges and defense mechanisms, we presented a categorization of security threats on the network functions virtualization and their characteristics. We also proposed possible solutions to address those threats. As future work, we will implement a testbed for an NFV framework with security resilience through simulation, emulation, or real implementation in order to prove our concepts for security in NFV.