Abstract
Microfluidic routing fabrics are reconfigurable primitives that permit the dynamic redirection of fluids on a flow-based microfluidic biochip. Such primitives are bringing the benefits of rapid prototyping and on-the-fly reconfigurability from integrated circuits to the microfluidic domain. An unfortunate side effect of this increased flexibility is susceptibility to tampering. A malicious adversary can alter either the electronic control signals or the pneumatic control lines used to drive the routing fabric. In this paper, we provide a high-level security assessment of microfluidic systems utilizing routing fabrics, and analyze their security under actuation tampering attacks. We show that under reasonable assumptions, the permissible states of a routing fabric form a probability distribution. We provide methods for efficiently determining this distribution through a binary tree representation. We then show how to synthesize routings fabrics that exhibit well-defined behaviors. We call a routing fabric designed in such a way tamper-mitigating, as it makes the effects of tampering probabilistically less severe. We then show how the proposed methodology can be used to protect a forensic DNA barcoding application from attack.
I. INTRODUCTION
Flow-based microfluidic biochips have emerged as an effective means of realizing the laboratory-on-a-chip [2], [3]. By integrating fluid handling channels and chambers, microvalvebased flow control, and sensors on elastomer substrates, many biochemical protocols once relegated to complex, manual laboratory procedures can now be performed efficiently and automatically in a miniaturized platform [4], [5]. Among the myriad of microfluidic technologies available today, flowbased microfluidics are one of the most developed and have been successfully commercialized in benchtop platforms such as the Fluidigm BioMark HD [6]. The latest research in flowbased biochips has drawn from well-established concepts in the semiconductor industry in an effort to manage increasing complexity while streamlining design, fabrication, and operation.
VIII. CONCLUSIONS
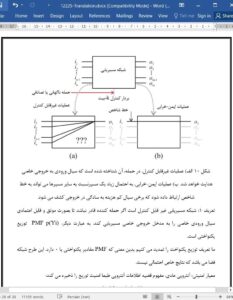
We presented a security assessment of an emerging microfluidic hardware primitive: the transposer-based routing fabric driven through a serial control line. We then formulated an analysis and design methodology under a random control vector attack model. Two classes of security, fail-safe and uncontrollable, were defined and case studies were presented to show how such characteristics could be leveraged in practice as a tamper mitigation mechanism. Such a design-time tamper mitigation technique eliminates one of the simplest methods for tampering with a physically vulnerable device employed at the point-of-care.