Abstract
With the growth of the scale of the market for Internet banking and e-commerce, the number of Internet-based financial markets has been increasing. Meanwhile, hacking incidents continuously affect the Internet-banking services. For this reason, a countermeasure is required to improve the security of the online identification process. The current security and authentication mechanisms applied to financial services, such as Internet banking services for 5G-enabled IoT, do not ensure security. In this paper, a transaction-linkage technique with which the designated terminal is combined is proposed to solve this fundamental problem. The technique improves the security of online identification mechanisms because it is possible to counteract all of the existing security threats. The proposed technique supports mutual authentication and is safe from eavesdropping attacks, replay attacks, spoofing attacks, and service-denial attacks. Moreover, the technique supports non-repudiation by storing the transaction history in a transaction-linkage device. We believe that the security of Internet-banking services for 5G-enabled IoT will be increased through the utilization of the proposed technique.
1. Introduction
With the growth of the scale of the market for Internet banking and ecommerce, the exchange of goods and services on the Internet has become a large part of the national economy [1]. Even though a variety of security techniques are applied in the processes of building these systems, hacking incidents still affect Internet banking services. Moreover, this kind of damage is continuous. Therefore, general security applications and techniques are needed for the online financial service to ensure security requirements such as confidentiality, integrity, availability, and non-repudiation [2]. Various cryptography-based mechanisms have been developed to satisfy these requirements over the past few decades, and their effectiveness was sufficiently proved through the utilization of proven mathematical tools [3]. Nevertheless, most of the security problems emerge in the process or the environment of applying the security techniques rather than in the cryptography-based technologies, so there is a need to research the vulnerabilities beyond the cryptography-based technologies and to identify measures that can counteract these vulnerabilities properly.
4. Conclusions
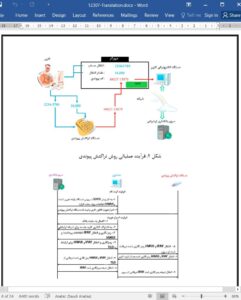
A designated PC service was adapted to restrict a terminal from using a service when the identity-verification methods supporting the existing Internet-banking services were under security threats. Nevertheless, the designated PC service did not pass the security assessment and did not define the evaluation criteria, so the service was still exposed to security threats. The existing transaction-linkage technique generated a linkage code by combining the transaction information with the secret information to counteract this problem. However, this technique was also exposed to various security threats. For these reasons, the current designated-PC service and transaction-linkage technique do not ensure security, so we proposed a transaction-linkage technique for which the designated terminal is combined to solve those problems. The proposed technique in this paper is capable of counteracting all of the mentioned security threats, thereby improving the online identity verification methods. We believe that the security of the Internet-banking services will be robustly supported by the application of the proposed protocol.