Abstract
The Internet of Things (IoT) brings together a large variety of devices of different platforms, computational capacities and functionalities. The network heterogeneity and the ubiquity of IoT devices introduce increased demands on both security and privacy protection. Therefore, the cryptographic mechanisms must be strong enough to meet these increased requirements but, at the same time, they must be efficient enough for the implementation on constrained devices. In this paper, we present a detailed assessment of the performance of the most used cryptographic algorithms on constrained devices that often appear in IoT networks. We evaluate the performance of symmetric primitives, such as block ciphers, hash functions, random number generators, asymmetric primitives, such as digital signature schemes, and privacy-enhancing schemes on various microcontrollers, smart-cards and mobile devices. Furthermore, we provide the analysis of the usability of upcoming schemes, such as the homomorphic encryption schemes, group signatures and attribute-based schemes.
1. Introduction
Nowadays, the Internet of Things (IoT) is a widely-discussed topic among researchers, engineers and technicians. IoT tends to be the next wave of innovation and there are many definitions of the IoT paradigm. For example, IoT can be defined as a highly interconnected network of heterogeneous entities such as tags, sensors, embedded devices, hand-held devices and back-end servers. IoT provides new services and applications that can be deployed in smart homes, transport applications (e.g. Vehicular Ad hoc Networks - VANETs), smart metering, smart grid, etc. Fig. 1 depicts the example of the IoT environment and shows some technologies and appliances that can be used in IoT.
5. Conclusion
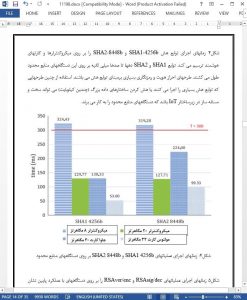
Many works and surveys discuss the security and privacy in the IoT. Nevertheless, only few concrete works present useful and applicable security solutions for IoT. This work presents the performance and memory limitations of current cryptographic primitives and schemes on various types of devices that can be used in IoT. Nowadays, symmetric ciphers and hash functions can be easily implemented into the IoT services that use constrained devices. These functions take only few milliseconds and can run on memory restricted microcontrollers with RAM less than 1 kB. Asymmetric cryptographic schemes and modular arithmetic operations can be used in the IoT services and applications as well. However, the devices should provide at least middle-sized RAM (e.g. > 4 kB) and storage memories (e.g. > 10 kB). Further, the time execution of some asymmetric cryptography functions and operations, for example, RSA signing by a 2048-bit private key, can cause a latency more than hundreds milliseconds on computationally constrained devices such as MSP microcontrollers, smart cards, etc. For example, applications that must sign and send data in real time cannot employ such computational expensive operations on restricted devices.