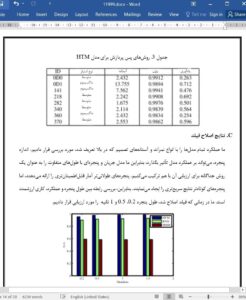
ABSTRACT
With the development of 5G and Internet of Vehicles technology, the possibility of remote wireless attack on an in-vehicle network has been proven by security researchers. Anomaly detection technology can effectively alleviate the security threat, as the first line of security defense. Based on this, this paper proposes a distributed anomaly detection system using hierarchical temporal memory (HTM) to enhance the security of a vehicular controller area network bus. The HTM model can predict the flow data in real time, which depends on the state of the previous learning. In addition, we improved the abnormal score mechanism to evaluate the prediction. We manually synthesized field modification and replay attack in data field. Compared with recurrent neural networks and hidden Markov model detection models, the results show that the distributed anomaly detection system based on HTM networks achieves better performance in the area under receiver operating characteristic curve score, precision, and recall.
I. INTRODUCTION
With the rapid development of mobile Internet, big data and cloud computing technology, the automobile gradually become intelligent, network oriented. The intelligent car network is a new direction of innovation and development. Concepts and technologies such as autopilot, shared car, and Internet of Vehicles (IoV) emerge as the times require. 5G is regarded by the industry as the key technology to realize automatic driving and network communication [1]. It has advantages of low delay, large bandwidth and high connection density. Moreover, most modern cars are equipped with multi-function remote information processing system, supporting global positioning system (GPS), media entertainment, or even directly accessing cellular networks. However, the remote information processing system is vulnerable to network attacks because it is connected to the external wireless network [2]–[4]. The attacker can access the target vehicle network through the wireless access interface [5], implement a variety of attacks such as replay attack, DoS attack, frame sniffing, frame injection and so on [6]–[8]. Thus, it brings potential security threats to the vehicle network.