Abstract
In this paper, a new cryptographic algorithm using a two-dimensional piecewise smooth nonlinear chaotic map is suggested. It depends on the confusion-diffusion model (permutation-substitution model). Firstly, the plain image is shuffled using the logistic map (confusion). Secondly, chaotic sequences are produced by two-dimensional piecewise smooth nonlinear chaotic map. Then, the produced sequences are preprocessed to integers between 0 and 255. Finally, the shuffled image is masked using the chaotic sequences (diffusion). The suggested algorithm is tested by different types of images. Furthermore, the decryption algorithm is implemented to retrieve the plain (original) image using the secret key. Experimental results and security analyses are applied using the suggested algorithm and its performances are validated with recent cryptographic algorithms. The security and performance analyses conclude that the suggested algorithm is secure, fast, and resists various attacks.
1. Introduction
In the current era where our lives depend on technology and the exchange of information, information security has become an important challenge. This information can take several forms, such as images, video, audio, text, and others. Moreover, images specifically have many applications in many sensitive areas, such as medical, military, and personal data, among others. This is why scientists are trying to protect the security of images while transferring them through various communication channels and preventing attacks that hackers may perform. The security of information can be achieved in three different ways: encryption, steganography and watermarking.
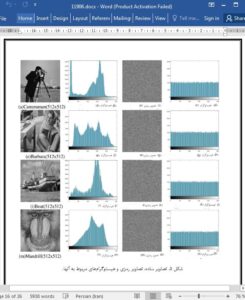
8. Conclusion
In this paper, a new cryptographic algorithm, based on a twodimensional piecewise smooth nonlinear chaotic map, has been proposed. 2DPSNCM produces chaotic sequences necessary to digital image encryption. NIST test has been executed on these sequences and it has confirmed that the 2DPSNCM is appropriate to digital image encryption. The security of the proposed algorithm has been proved over many experimental analyses: histogram analysis, information entropy analysis, correlation analysis, sensitivity analyses, key space analysis, noise attack analysis, and chosen plaintext attack analysis. The experimental results have concluded that the proposed algorithm can be used to image encryption efficiently. Finally, the quantum image encryption algorithm via 2DPSNCM will be proposed to increase the current algorithm’s security in the future.